IMS is Not That Secure on Your 5G/4G Phones
May 29, 2024· ,,,,,,,,·
0 min read
,,,,,,,,·
0 min read
Jingwen Shi
Sihan Wang (Co-Primary)
Min-Yue Chen
Guan-Hua Tu
Tian Xie
Man-Hsin Chen
Yiwen Hu
Chi-Yu Li
Chunyi Peng
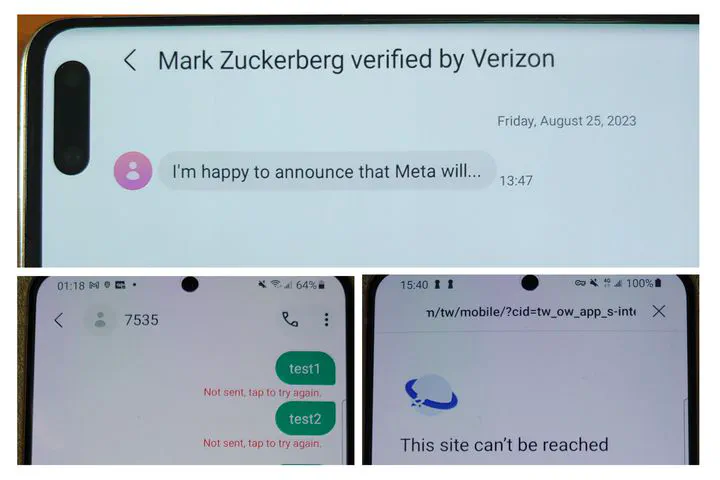 Image credit:
Image credit:Abstract
IMS (IP Multimedia Subsystem) is vital for delivering IP- based multimedia services in mobile networks. Despite constant upgrades by 3GPP over the past two decades to support heterogeneous radio access networks (e.g., 4G LTE, 5G NR, and Wi-Fi) and enhance IMS security, the focus has primarily been on cellular infrastructure. Consequently, IMS security measures on mobile equipment (ME), such as smartphones, lag behind rapid technological advancements. Our study reveals that mandated IMS security measures on ME fail to keep pace, resulting in new vulnerabilities and attack vectors, including denial of service (DoS) across all networks, named SMS source spoofing, and covert communications over Video-over-IMS attacks. All vulnerabilities and proof-of-concept attacks have been experimentally validated in operational 5G/4G networks across various phone models and network operators. Finally, we propose and prototype standard-compliant remedies for these vulnerabilities.
Type
Publication
In ACM MobiCom ‘24 Proceedings of the 30th Annual International Conference on Mobile Computing and Networking