When Good Turns Evil: Encrypted 5G/4G Voice Calls Can Leak Your Identities
Oct 2, 2023· ,,,,,,,,,,·
0 min read
,,,,,,,,,,·
0 min read
Jingwen Shi
Tian Xie
Guan-Hua Tu
Chunyi Peng
Chi-Yu Li
Andrew Hou
Sihan Wang
Yiwen Hu
Min-Yue Chen
Li Xiao
Xiaoming Liu
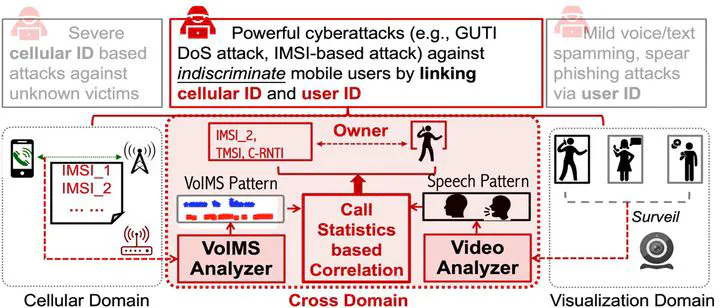 Image credit:
Image credit:Abstract
5G/4G voice calls are always encrypted for security and privacy. However, in this work, we unveil several vulnerabilities which can unintentionally leak 5G/4G call state information, despite encryption protection. They stem from recent call optimization techniques standardized in the 3GPP specifications and adopted by mobile network operators. While these techniques are effective to enhance 5G/4G call quality and efficiency, they unfortunately expose extra call information, which can be exploited to precisely infer call states and launch side-channel attacks. By leveraging precise call states, we devise a Cross-domain Identity Linkage attack, CrossIL, which aims to infer mobile users’ user identities and cellular identities, thereby enabling powerful cyberattacks or privacy inferences against high-value victims. We have experimentally validated these vulnerabilities and assessed the attack damages with three major U.S. carriers. Our experimental result shows that the success rate on the identity inference ranges from 89% to 98%. Finally, we propose and evaluate a cellular-friendly solution.
Type
Publication
2023 IEEE Conference on Communications and Network Security