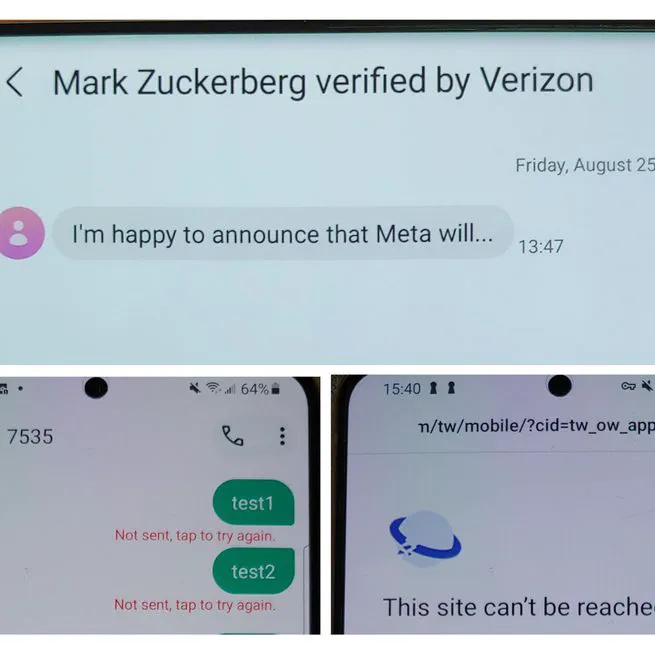
Mobicom '24 - IMS security measures on mobile devices lag behind advancements, leading to vulnerabilities like DoS, SMS spoofing, and covert communications, all validated in 5G/4G networks, with proposed standard-compliant remedies.
May 29, 2024

Cellular emergency services for anonymous users introduce vulnerabilities that allow free data, DoS, and denial of service attacks, validated in U.S. and Taiwan networks, with proposed standard-compliant remedies.
Mar 1, 2024
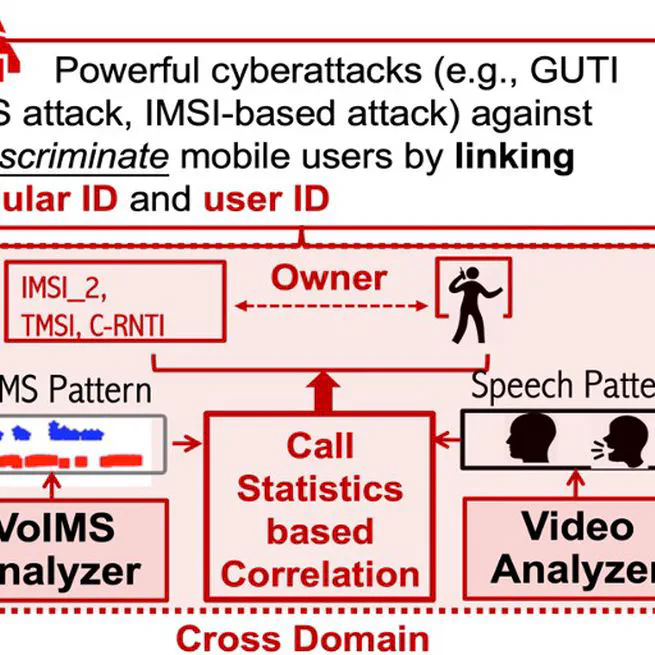
This study uncovers vulnerabilities in 5G/4G call optimization techniques that, despite encryption, can leak call state information, enabling side-channel attacks like Cross-domain Identity Linkage (CrossIL) with identity inference success rates of up to 98\%.
Oct 2, 2023
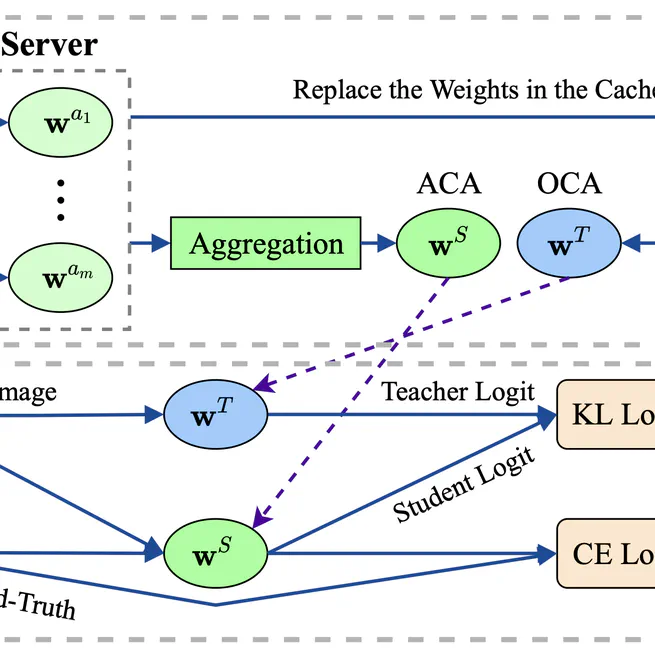
FedKF addresses model drift in federated learning by fusing global and local knowledge during training, improving performance and fairness through techniques like active–inactive model aggregation and data-free knowledge distillation.
Sep 27, 2023

Mobicom '22 - Cellular emergency services, especially for anonymous users, increase the attack surface, leading to vulnerabilities enabling free data usage, DoS, and denial of emergency services.
Oct 14, 2022